In today’s digital age, cybersecurity threats are becoming increasingly sophisticated, and it’s more important than ever for organizations to have a solid understanding of their cybersecurity risk landscape.
One way to do this is by identifying key risk indicators (KRIs) to help organizations monitor and manage their cybersecurity risks effectively.
KRIs are specific metrics or data points that help organizations understand the level of risk they face in their environment.
Tracking these indicators allows organizations to proactively identify and address potential cybersecurity issues before they escalate into significant cyber incidents.
Kris can also help organizations prioritize cybersecurity efforts and allocate resources more effectively.
Identifying KRIs requires a comprehensive understanding of an organization’s unique risk landscape. This process begins with a thorough risk assessment considering the organization’s size, industry, regulatory environment, and specific threats.
Once the risk assessment is complete, organizations can identify the KRIs that are most relevant to their environment and develop a monitoring and reporting framework to track these indicators over time.
Doing so enables organizations to gain valuable insights into their cybersecurity posture and take proactive steps to mitigate risks and protect their critical assets.
Understanding Cybersecurity Risks
Cybersecurity risks are the potential threats that an organization faces when using digital technologies. These risks can arise from various sources, including external attackers, insiders, or even accidents caused by human error. Understanding these risks is essential for organizations to develop effective cybersecurity strategies.
The Cyber Risk Landscape
The cyber risk landscape constantly evolves, and organizations must keep up with the latest threats to stay protected. Cyber risks can be classified into different categories, such as malware, phishing, ransomware, and denial-of-service attacks.
Common Cybersecurity Threats
Cybersecurity threats are malicious activities that can compromise an organization’s information systems’ confidentiality, integrity, or availability. Some common cybersecurity threats include:
- Malware: Malware is a type of software designed to damage or disrupt computer systems. It can take many forms, including viruses, worms, and Trojans.
- Phishing: Phishing is a type of social engineering attack that attempts to trick users into revealing sensitive information, such as login credentials or financial data.
- Ransomware: Ransomware is a type of malware that encrypts an organization’s files and demands payment in exchange for the decryption key.
The Importance of Risk Assessment
Risk assessment is the process of identifying, analyzing, and evaluating potential risks to an organization’s information systems. This process is essential for developing effective cybersecurity strategies and identifying key risk indicators (KRIs) to monitor.
Conducting a risk assessment allows organizations to identify their most critical assets, evaluate the likelihood and impact of potential threats, and develop a risk management plan to mitigate these risks.

This plan may include implementing security controls, training employees, and developing incident response plans.
Understanding cybersecurity risks is essential for organizations to develop effective cybersecurity strategies. The cyber risk landscape constantly evolves, and organizations must keep up with the latest threats to stay protected.
Organizations can mitigate potential risks and protect their critical assets by conducting a risk assessment and identifying key indicators.
Identifying Key Risk Indicators (KRIs)
Identifying Key Risk Indicators (KRIs) is essential to managing cybersecurity risks. KRIs are metrics that enable organizations to identify and assess the level of risk associated with their cybersecurity posture.
They help organizations monitor and track the effectiveness of security controls, identify vulnerabilities and threats, and measure the overall risk level of an organization’s IT infrastructure.
Defining KRIs in Cybersecurity
KRIs in Cybersecurity can be defined as metrics that help organizations measure the likelihood that the combined probability of an event and its consequences will exceed the organization’s risk appetite and have a profoundly negative impact on an organization’s ability to be successful.
KRIs help organizations to identify and quantify risks, assess the effectiveness of existing controls, and make informed decisions about risk management.
Examples of Cybersecurity KRIs
There are many different types of Cybersecurity KRIs that organizations can use to measure risk. Some examples of Cybersecurity KRIs include:
- Number of phishing emails received per day.
- Number of malware infections per month.
- Percentage of systems with up-to-date antivirus software.
- Number of failed login attempts per day.
- Percentage of employees who have completed cybersecurity awareness training.
Setting Thresholds and Benchmarks
Setting thresholds and benchmarks is an essential part of using KRIs effectively. Thresholds are the levels at which a KRI indicates that a risk is present and action is required.
Benchmarks are the levels at which a KRI indicates that an organization is performing well.
To set thresholds and benchmarks, organizations must first define their risk appetite. Risk appetite is the level of risk that an organization is willing to accept in pursuit of its objectives.
Once the risk appetite is defined, organizations can set thresholds and benchmarks that align with their risk appetite.
Identifying Key Risk Indicators (KRIs) is essential to managing cybersecurity risks. KRIs help organizations to identify and quantify risks, assess the effectiveness of existing controls, and make informed decisions about risk management.
Setting thresholds and benchmarks that align with their risk appetite, organizations can use Key Risk Indicators (KRIs) to monitor and track the effectiveness of security controls, identify vulnerabilities and threats, and measure the overall risk level of an organization’s IT infrastructure.
Risk Management and Compliance
Effective cybersecurity risk management requires a comprehensive understanding of the organization’s unique risk landscape.
This involves identifying and monitoring Key Risk Indicators (KRIs), which are metrics capable of showing that the enterprise is, or has a high probability of being, subject to a risk that exceeds the defined risk appetite.
Integrating KRIs into Risk Management
Integrating KRIs into risk management can provide a more holistic view of an organization’s risk profile. Tracking and analyzing Key Risk Indicators (KRIs) allows organizations to identify and analyze risks and proactively mitigate potential risks.
It is important to note that KRIs should be aligned with the organization’s risk appetite and reviewed periodically to ensure they remain relevant.
Compliance and Regulatory Requirements
Compliance and regulatory requirements are critical considerations in cybersecurity risk management. Organizations must ensure they comply with applicable laws, regulations, and industry standards.
Failure to comply with these requirements can result in significant financial and reputational damage.
Reporting and Transparency
Effective reporting and transparency are essential components of cybersecurity risk management. Organizations must be able to provide accurate and timely information on their risk profile to stakeholders, including senior management, the board of directors, and external auditors.
This requires robust documentation and reporting processes that provide clear and concise information on the organization’s risk profile and management activities.
Effective cybersecurity risk management requires a comprehensive understanding of an organization’s unique risk landscape.
This involves identifying and monitoring KRIs, integrating KRIs into risk management, ensuring compliance with regulatory requirements, and providing accurate and transparent reporting on the organization’s risk profile.
Operationalizing KRIs
Once an organization has identified its Key Risk Indicators (KRIs) for cybersecurity, it is essential to operationalize them.
This means integrating them into the organization’s day-to-day activities so they become a natural part of the cybersecurity risk management process.
Monitoring and Responding to KRIs
One way to operationalize KRIs is to monitor them regularly and respond promptly when they indicate a potential risk. This requires setting up a system to track and analyze the KRIs continually.
The system should be able to generate alerts when a KRI exceeds a predefined threshold, indicating a potential risk. The alerts should be sent to the relevant personnel, who can investigate and appropriately respond to the risk.
Cybersecurity Policies and Procedures
Another way to operationalize KRIs is to integrate them into cybersecurity policies and procedures. The policies and procedures should spell out how the KRIs will be monitored, who will be responsible for monitoring them, and what actions will be taken when a KRI indicates a potential risk.
This will ensure that the KRIs are not seen as an add-on but rather as an integral part of the organization’s cybersecurity risk management process.
Training and Employee Awareness
Operationalizing KRIs also involves training employees on their significance and how to respond to them. Employees should be made aware of the KRIs that are relevant to their roles and responsibilities, how they will be monitored, and what actions they should take when a KRI indicates a potential risk.
This will help ensure that the KRIs are not seen as something only the IT department needs to worry about but rather as something that every employee needs to be aware of.
Operationalizing KRIs for cybersecurity involves integrating them into the organization’s day-to-day activities, policies, and procedures.
It also involves monitoring them regularly, responding promptly when they indicate a potential risk, and training employees on their significance.
Doing so ensures that Key Risk Indicators (KRIs) become an integral part of an organization’s cybersecurity risk management process, helping to avoid potential threats.
Technological Considerations
When identifying key cybersecurity risk indicators, it is important to consider various technological factors impacting an organization’s security posture.
This section explores some of the key technological considerations organizations should consider.
Security Measures and Controls
One of the most critical technological considerations for cybersecurity risk management is the implementation of security measures and controls.
These measures and controls are implemented to protect an organization’s assets from cyber threats. Examples of security measures and controls include firewalls, intrusion detection systems, antivirus software, and encryption.
Organizations must ensure these security measures and controls are properly configured and maintained to provide maximum protection against cyber threats.
Regular security assessments and vulnerability scans can help identify gaps in security measures and controls, allowing organizations to take corrective action before cyber incidents occur.
The Role of IT in Cybersecurity
It plays a crucial role in cybersecurity risk management. IT professionals are responsible for implementing and maintaining the security measures and controls that protect an organization’s assets. They also play a key role in detecting and responding to cyber incidents.
Organizations must ensure their IT staff are properly trained and equipped to handle cybersecurity risks. This includes providing ongoing training on the latest threats and vulnerabilities and ensuring that IT staff can access the latest tools and technologies for detecting and responding to cyber incidents.
Internet of Things (IoT) and Cyber Risk
The Internet of Things (IoT) has introduced new cybersecurity risks for organizations. IoT devices are often connected to corporate networks, creating new entry points for cyber threats.
These devices can also be difficult to secure, as they often lack traditional IT systems’ security measures and controls.
Organizations must take steps to protect their networks from IoT-related cyber risks. This includes implementing security measures and controls specifically designed for IoT devices, such as network segmentation and device authentication.
It also involves ensuring that IoT devices are properly configured and maintained to minimize the risk of cyber incidents.
Organizations must consider various technological factors when identifying key cybersecurity risk indicators. This includes implementing security measures and controls, ensuring that IT staff are properly trained, and addressing the unique cybersecurity risks posed by IoT devices.
Taking these steps allows organizations to better protect themselves from cyber threats and minimize the impact of cyber incidents.
Incident Management and Recovery
In the event of a cyber-attack, an organization’s ability to respond quickly and effectively is critical to minimizing damage and preventing further harm. Incident management and recovery are key components of any cybersecurity strategy.
Cyber Incident Response Planning
To ensure a timely and effective response to a cyber incident, organizations should have a cyber incident response plan (CIRP) in place.
A CIRP is a documented set of procedures that outlines the steps to be taken during a cyber attack. It should include incident response roles and responsibilities, communication plans, and procedures for identifying, containing, and mitigating the attack.
An effective CIRP should also include early warning systems that can detect potential cyber attacks before they occur.
This can include monitoring for suspicious activity on the network, analyzing system logs, and conducting vulnerability assessments. Organizations can proactively mitigate risk and prevent damage by detecting potential threats early.
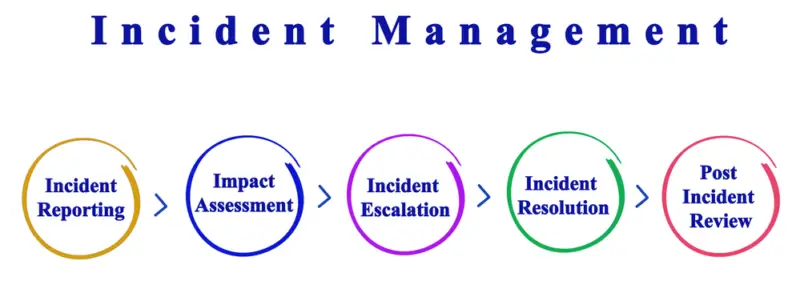
Recovery Strategies and Backup Plans
In addition to incident response planning, organizations should also have recovery strategies and backup plans in place.
Recovery strategies are the procedures and processes to restore systems and data after a cyber attack. Backup plans are the procedures and processes to create and maintain copies of critical data and systems.
Recovery strategies should be designed to minimize downtime and data loss. This can include using redundant systems, implementing disaster recovery plans, and regularly testing recovery procedures.
Backup plans should include regularly backing up critical data and systems, storing backups offsite, and regularly testing backups to ensure their integrity.
Effective incident management and recovery plans enable organizations to minimize the damage caused by cyber-attacks and quickly restore operations.
Measuring Effectiveness and Progress
Measuring the effectiveness of cybersecurity programs is an essential component of risk management. It helps organizations identify gaps in their security posture and make informed decisions on allocating resources.
This section will discuss two critical aspects of measuring effectiveness and progress in cybersecurity: key performance indicators (KPIs) and benchmarking.
Key Performance Indicators (KPIs)
KPIs are metrics that organizations use to measure the effectiveness of their cybersecurity programs. They provide a way to track progress toward goals and objectives, identify areas for improvement, and make informed decisions.
KPIs should align with the organization’s goals and objectives and be relevant, measurable, and actionable.
Examples of KPIs that organizations can use to measure the effectiveness of their cybersecurity programs include:
- The number of security incidents.
- Time to detect and respond to security incidents.
- Percentage of systems with up-to-date patches.
- Percentage of employees who complete cybersecurity training.
- A number of vulnerabilities were identified and remediated.
- Percentage of critical assets with adequate security controls in place.
Organizations should regularly review their KPIs to ensure they remain relevant and aligned with their goals and objectives. They should also use predictive analytics to identify and proactively mitigate potential risks.
Benchmarking and Comparative Analysis
Benchmarking compares an organization’s cybersecurity program to industry best practices or other organizations with similar characteristics.
It provides a way to identify areas for improvement and measure progress over time. Comparative analysis is a similar process that compares an organization’s cybersecurity program to its previous performance.
Organizations should use benchmarking and comparative analysis to identify gaps in their security posture and make informed decisions on allocating resources. They should also use benchmarking to identify areas where they are performing well and share those best practices across the organization.
Measuring the effectiveness and progress of cybersecurity programs is a critical component of risk management. Organizations should use KPIs to track progress toward goals and objectives and regularly review them to ensure they remain relevant.
They should also use benchmarking and comparative analysis to identify areas for improvement and measure progress over time.

Advanced Topics in Cybersecurity Risk
Machine Learning and Predictive Analytics
Machine learning and predictive analytics are powerful tools that can be used to identify potential cyber threats. These tools use data from various sources to create models that can predict future events.
By analyzing data patterns, machine learning algorithms can identify anomalies that may indicate a potential cyber attack.
Predictive analytics can also be used to identify vulnerabilities in systems and applications, allowing organizations to take proactive measures to prevent attacks.
One of the key benefits of machine learning and predictive analytics is that they can automate the process of identifying potential threats.
This can save organizations time and resources, as they no longer need to review logs and other data sources manually.
Instead, machine learning algorithms can analyze data in real-time, providing organizations with up-to-date information about potential threats.
Third-Party and Supply Chain Risks
Third-party and supply chain risks are a growing concern for organizations of all sizes. These risks arise when organizations rely on third-party vendors or suppliers to provide critical services or products.
If these vendors or suppliers are compromised, they can introduce vulnerabilities into the organization’s systems and applications.
Organizations should conduct thorough risk assessments of their vendors and suppliers to mitigate third-party and supply-chain risks.
This may involve reviewing their security policies, procedures, and track records for security incidents. Organizations should also consider implementing security controls that limit third-party vendors and suppliers’ access to their systems and data.
Machine learning, predictive analytics, and effective third-party and supply chain risk management can help organizations avoid potential cyber threats.
Taking a proactive approach to cybersecurity risk management, organizations can reduce the likelihood of a malicious attack or fraud and improve their overall security posture.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.

