Every business needs to have a secure IT infrastructure. The Security Risk Analysis Mips (Mandatory Information Protection Standard) defines the security requirements for any organization that stores or processes protected data. It is designed to help organizations identify and mitigate any potential risks associated with their IT systems.
In the ever-evolving world of technology, businesses and individuals alike must stay vigilant in their efforts to protect sensitive data and maintain the integrity of their systems. One important aspect of this is understanding and conducting security risk analysis for MIPS (Merit-based Incentive Payment System) – a critical component in ensuring a secure and efficient healthcare environment.
In this blog post, we will delve into the importance of security risk analysis for MIPS, discuss the key steps involved, and provide valuable tips for effectively mitigating potential security risks.

Why Security Risk Analysis Matters for MIPS
MIPS is a value-based payment model implemented under the Medicare Access and CHIP Reauthorization Act (MACRA) for eligible healthcare providers. The program aims to improve patient care and reduce healthcare costs by rewarding providers based on their performance across four categories: Quality, Cost, Improvement Activities, and Promoting Interoperability.
Among these categories, Promoting Interoperability stands out as the most relevant to security risk analysis. It focuses on the secure and efficient exchange of electronic health information, requiring providers to demonstrate their commitment to protecting patient data and maintaining compliance with the Health Insurance Portability and Accountability Act (HIPAA).
Failure to perform adequate security risk analysis could lead to data breaches, financial penalties, and reputational damage, ultimately affecting patient trust and overall performance within the MIPS program.
Steps to Conduct a Security Risk Analysis for MIPS
Scope and Data Collection:
Before initiating the risk analysis, determine the scope of your assessment. This involves identifying all electronic health information (EHI) systems and components within your organization, including hardware, software, and network infrastructure. Collect relevant documentation and policies to support your analysis.
Risk Assessment:
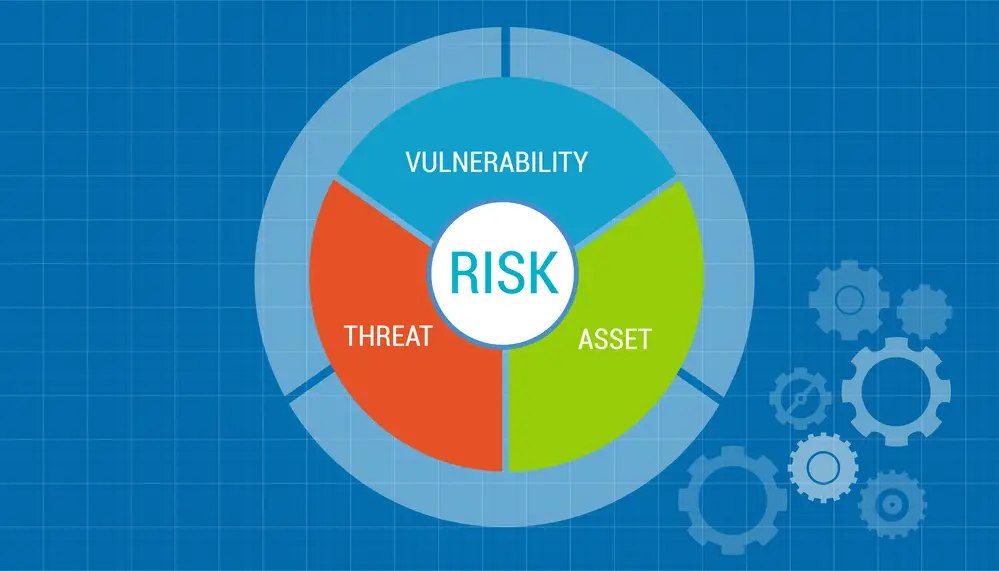
Perform a thorough assessment of potential vulnerabilities and threats to your EHI systems. This could include unauthorized access, malware, data breaches, or natural disasters. Assess the likelihood and potential impact of each threat and vulnerability to establish a risk level (low, medium, or high).
Implement Security Measures:
Based on your risk assessment, develop and implement appropriate security measures to address the identified vulnerabilities and threats. This could involve updating software, using security updates improving access controls, or implementing encryption solutions.
Documentation and Reporting:
Document the entire risk analysis process, including the scope of security rule, risk assessment, security measures implemented, and any residual risks. This documentation will serve as evidence of your organization’s commitment to security and compliance with MIPS requirements.
Continuous Monitoring and Improvement:
Security risk analysis should not be a one-time event. Regularly review and implement security updates to update your risk assessment, security measures, and documentation to stay ahead of emerging threats and maintain compliance with MIPS requirements.
Tips for Effective Security Risk Analysis in MIPS
Adopt a Holistic Approach: Consider all aspects of your organization’s EHI systems, including people, processes, and technology. This will help ensure a comprehensive understanding of potential risks and vulnerabilities.
Engage Stakeholders: Involve key stakeholders in the risk analysis process, such as IT staff, clinical staff, and leadership. This will help create a culture of security awareness and shared responsibility.
Leverage Risk Assessment Tools: There are numerous risk assessment tools and frameworks available, such as the NIST Cybersecurity Framework and the HHS Security Risk Assessment Tool. Utilize these resources to guide and enhance your risk analysis process.
Address Human Factors: Training and awareness programs play a critical role in mitigating security risks. Educate your staff about potential threats, security best practices, and organizational policies and procedures.
What is Security Risk Analysis Mips?
Security Risk Analysis Mips is a set of standards developed by the government of the United Kingdom in order to ensure that organizations are aware of and actively manage the risks associated with storing or processing protected data.
The standards consist of six components: monitoring, protection, risk assessment, training, awareness, and compliance. Each component contains specific objectives that must be implemented in order for an organization to comply with the standard.
Conduct a Security Risk Assessment in accordance with the statutory requirements in 45 CFR 1644.308(1), which includes assessing security in ePHI information created in certified electronic health records (CEHRT) according to the requirements of certification. This is a necessary measure for Promoting Interoperable Performance Category and must be answered by PI to be successful reporting.
How to Perform Your Risk Analysis
The requirement for risk analysis is problematic due to the lack of specific steps required to achieve these objectives. It’s difficult to implement a single-size-fits-all compliance strategy because practices vary widely.
I want people to understand basic knowledge. The risk analysis is simply an extension of HIPAA privacy regulations — and if you are implementing this requirement, you are likely to be complying with HIPAA,” a spokesperson said. Five aspects should be analyzed.
In the ever-changing arena of health information technology cybersecurity, correcting identified security deficiencies is a vital part of staying ahead of the curve.
This begins with an accurate and thorough assessment of your organization’s systems, enabling you to pinpoint vulnerabilities and develop targeted strategies for addressing them.
Through correcting identified security deficiencies, you lay the foundation for a strong defense against potential threats. Technical safeguards, such as access controls, encryption, and intrusion detection systems, serve as the building blocks for this robust security framework.
Together, these measures create a synergistic force that safeguards your organization’s sensitive information, fosters a culture of vigilance, and ensures compliance with critical standards like MIPS and correct identified security deficiencies.
How Can You Use Security Risk Analysis Mips?
The best way to use Security Risk Analysis Mips is by understanding what it entails and implementing its principles into your day-to-day operations. Doing so will allow you to identify potential risks before they become actual threats and ultimately reduce the likelihood of a breach occurring within your organization.
Furthermore, having an understanding of the standards can also help you develop more effective policies and procedures when it comes to protecting sensitive information.
At the core of every healthcare interaction lies the delicate balance between access to essential patient health information and the need to protect it from unauthorized use. As more healthcare providers and organizations transition to electronic systems, ensuring the security of electronic protected health information (ePHI) becomes a top priority.
Medicaid services, like other healthcare programs, are deeply intertwined with the exchange of sensitive patient data, necessitating a strong commitment to protecting patient health information.
Through fostering a culture of cybersecurity awareness and implementing robust safeguards, healthcare providers not only demonstrate their dedication to patient trust but also contribute to a more secure and efficient healthcare landscape, where better outcomes are achieved through the responsible use and protection of vital health data.
What Are Some Benefits of Using Security Risk Analysis Mips?
Using Security Risk Analysis Mips can provide numerous benefits for your organization including improved security, increased visibility into potential issues, reduced costs associated with breaches, and better regulatory compliance.
Additionally, having an understanding of the standards can also help you create an effective information security program which will ultimately reduce overall risk within your organization as well as ensure that all employees are trained on proper procedures for handling sensitive information.
Conclusion
In summary, implementing Security Risk Analysis Mips can help organizations improve their overall security posture by helping them identify potential risks before they become actual threats as well as reducing costs associated with breaches if they should occur.
Additionally, having an understanding of the standards can also help organizations develop better policies and procedures when it comes to protecting sensitive data which will ultimately result in improved compliance with relevant regulations.
Security risk analysis is a vital component of MIPS and is essential for maintaining the confidentiality, integrity, and availability of electronic health information. By following the steps outlined above and adopting a proactive, continuous approach to risk management, healthcare providers can minimize

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.