In an era where cyber threats are evolving rapidly and security breaches make headlines, the importance of a robust and adaptive approach to managing risk cannot be overstated.
The Security Risk Management Lifecycle is a crucial framework that enables organizations to proactively identify, assess, mitigate, and monitor risks to protect their most valuable digital assets.
Dive into this comprehensive guide as we unravel the intricacies of the Integrated Adaptive Management Model (IAMM) and share actionable insights to empower you with the knowledge and tools needed for implementing effective risk management strategies.
Discover how mastering the Security Risk Management Lifecycle will bolster your organization’s cybersecurity posture and ensure business continuity, compliance, and sustained growth in an increasingly connected world.NIST offers guidance for information security risks in US companies.
All these scenarios of cyber-threats lead to the growth and development of Information Security Risk Management, a critical aspect of any organization’s cybersecurity strategy.
In this blog post, we will explore the Risk Management Lifecycle, focusing on the Integrated Adaptive Management Model (IAMM), and provide insights into effective strategies for monitoring actions, managing risks, and implementing security control profiles.

What is Information Security Risk Management?
Information Security Risk Management is the process of identifying, assessing, and mitigating risks to an organization’s digital assets and operations. This discipline aims to protect critical information, maintain business continuity, and safeguard the organization’s reputation.
It is also an approach for identifying risks and managing risks associated with information technology. It involves identifying, assessing, and managing risks affecting an organization’s confidentiality, integrity, and availability.
This approach aims primarily at treating risk in the light of organizational risk tolerance. Businesses with risk appetite should not expect to eliminate risks but seek to determine acceptable risks to their organization.
Risk Management Lifecycle (IAMM)
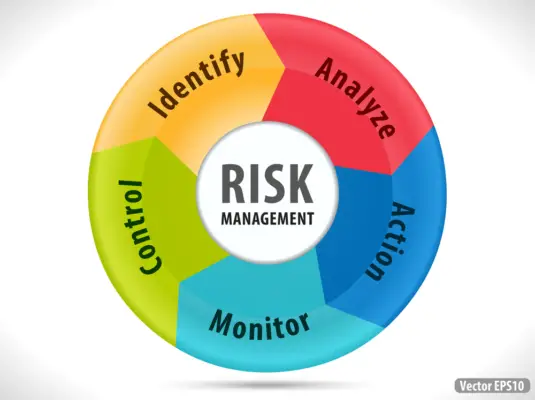
The Risk Management Lifecycle is a continuous process of identifying, assessing, mitigating, and monitoring security risks. The Integrated Adaptive Management Model (IAMM) is a widely recognized framework for implementing risk management processes, the life cycle consists of four main stages:
Identify: The first step involves identifying potential risks to the organization’s information assets. This includes conducting a comprehensive risk assessment, mapping out the organization’s digital landscape, and identifying vulnerabilities, threats, and potential attack vectors.
Assess: Once risks are identified, they must be assessed based on their likelihood of occurrence and potential impact on the organization. This helps prioritize and mitigate risks, and allocate resources accordingly.
Mitigate: The third stage involves developing and implementing appropriate risk mitigation strategies, such as applying security controls, modifying business processes, or investing in new technologies.
Monitor: The final stage involves ongoing monitoring and evaluation of the implemented mitigation strategies, ensuring they remain effective and adapting them as necessary to address new or evolving risks.
Monitoring Your Actions
Continuous monitoring is essential for maintaining an effective enterprise risk management program. Organizations can stay ahead of emerging threats and vulnerabilities by regularly reviewing and updating risk assessments. Key components of an effective monitoring process include:
Periodic risk assessments: Conducting regular risk assessments helps identify new risks and ensures the organization’s risk profile remains up-to-date.
Incident tracking and analysis: Tracking and analyzing security incidents can provide valuable insights into the effectiveness of existing risk management strategies and identify areas for improvement.
Compliance monitoring: Regularly reviewing compliance with industry standards and regulations can help identify potential gaps in security controls and ensure the organization remains compliant.
Performance metrics: Establishing and tracking performance metrics can help evaluate the effectiveness of risk management activities and identify areas for improvement.
Managing Information Security Risks Throughout the Project Lifecycle
Effective risk management should be integrated into all stages of a project’s lifecycle, from initiation to closure. It ensures that security considerations are factored into every decision and helps to minimize potential risks. Key steps in operational risk, include:
Initiation: During the project initiation stage, identify potential risks and establish a risk management plan outlining how risks will be identified, assessed, mitigated, and monitored throughout the project.
planning: During the planning stage, incorporate risk management activities into the overall project plan, including allocating resources, establishing timelines, and setting performance metrics.
Execution: Implement the risk management plan during the execution stage, ensuring that risk mitigation strategies are effectively executed and monitored.
Closure: Review the effectiveness of the project managers’ risk management plan during the project closure stage, identifying lessons learned and areas for improvement.
IT Security Risk Management Process
The IT Security Risk Management Process involves a series of steps designed to identify, assess, mitigate, and monitor risks specific to an organization’s IT infrastructure. These steps include:
Asset inventory:
Start by creating a comprehensive inventory of your IT assets, such as hardware, software, and data assets. Make sure to include their respective locations and ownership within your organization.
Keeping an up-to-date asset inventory helps you better understand your IT landscape, identify potential vulnerabilities, and determine where additional security measures may be needed.
Risk identification:
How should one determine the potential risks of the proposed project? The risk management process involves different methods; It’s called the risk register and provides the foundation of most risk management processes.
Identify potential risks to IT assets, including vulnerabilities, threats, and attack vectors. Consider both internal and external sources of risk, such as employee behavior, third-party vendors, and natural disasters.
As you work on identifying potential risks to your IT assets, keep in mind the various vulnerabilities, threats, and attack vectors that could impact your system level or organization. Be thorough in your examination, taking into account both internal and external sources of risk.
For example, consider the role of employee behavior in exposing your systems to threats and the potential vulnerabilities introduced by third-party vendors. Additionally, don’t overlook the potential impact of natural disasters on your IT infrastructure.
Risk assessment:
When you’re assessing each identified risk, evaluate it based on the likelihood of occurrence and its potential impact on your organization’s IT infrastructure. This critical step will enable you to determine which risks require the most attention and resources.
Prioritize risks in this manner, you can effectively allocate your resources and focus your efforts on addressing the most significant threats to your organization, ultimately strengthening your IT security posture.
Assess each identified risk based on its likelihood of occurrence and potential impact on the organization’s IT infrastructure.
Risk mitigation:
As you move forward with risk mitigation, focus on developing and implementing strategies tailored to your organization’s specific risks. This may involve applying security controls, updating software, or creating incident response plans.
Remember that it’s important to consider proactive and reactive measures when addressing risks. Proactively securing your IT infrastructure will help prevent potential threats, while reactive measures ensure you’re prepared to respond effectively when incidents occur.
Risk monitoring and review:
In the risk monitoring and review stage, it’s essential to stay vigilant and continuously evaluate the effectiveness of your implemented risk mitigation strategies. Make adjustments as necessary to address new or evolving risks that may arise.
Don’t forget to regularly review risk assessments and update your organization’s risk profile to ensure it remains accurate and up-to-date.

Departmental IT Security Risk Management Activities
As you oversee Departmental IT Security Risk Management Activities, ensuring that every department in your organization effectively addresses its unique risks and maintains a secure environment is important. Focus on these key activities
Department-specific risk assessments: Conduct risk assessments specific to each department, considering the unique IT assets, processes, and potential threats associated with each department’s operations.
Security awareness training: Provide department-specific security awareness training to employees, ensuring they understand the risks associated with their role and how to mitigate them.
Incident response planning: Develop and implement department-specific incident response plans outlining how the department will respond to and recover from security incidents.
Monitoring and reporting: Monitor departmental IT security risk management activities and report their effectiveness to senior management. This can help identify areas for improvement and ensure that resources are allocated effectively.
Information System Security Risk Management Activities
Information System Security Risk Management Activities focus on securing an organization’s information systems and ensuring critical data’s confidentiality, integrity, and availability. Key activities include:
System-specific risk assessments:
Conduct risk assessments specific to each information system, considering the unique risks, vulnerabilities, and potential threats associated with each system.Security controls implementation: Implement appropriate security controls for each information system, using key principles such as encryption, access controls, and intrusion detection systems.
System hardening: Harden information systems by applying security patches, disabling unnecessary services, and configuring settings to reduce the attack surface.
Continuous monitoring: Continuously monitor information systems for signs of potential security incidents, such as unauthorized access or suspicious activity.
Security Control Profiles
Security Control Profiles are predefined sets of security controls designed to address specific risks, regulatory requirements, or industry standards.
Defining risk control strategies
Risk mitigation involves the use of control strategies and a careful response plan. You should designate an employee responsible for the risks in their organization using the responsibility chart.
The best risk response is based on the sorted Risk List done during the previous steps. Take into account their urgency and priority: some need immediate attention and others may need immediate solutions.
Implement these profiles, organizations can streamline their risk management activities and ensure compliance requirements are met. Examples of Security Control Profiles include:
Payment Card Industry Data Security Standard (PCI DSS): A set of security controls designed to protect cardholder data and ensure the secure processing of credit card transactions.
Health Insurance Portability and Accountability Act (HIPAA) Security Rule: A set of security controls designed to protect electronic protected health information (ePHI) and ensure health information’s confidentiality, privacy risk integrity, and availability.
NIST Cybersecurity Framework (CSF): A set of security controls designed to help organizations manage and reduce cybersecurity risk in alignment with industry best practices.
ISO/IEC 27001: A set of security controls designed to help organizations establish, implement, maintain, and continually improve an Information Security Management System (ISMS).
Conclusion
In conclusion, the Security Risk Management Lifecycle is a crucial framework that allows you to proactively and effectively manage your organization’s IT security risks. Understanding and implementing the different stages of this lifecycle, you can ensure the protection of your organization’s digital assets, maintain business continuity, and comply with relevant regulations and standards.
In a constantly evolving digital landscape, staying ahead of emerging threats and continuously adapting your risk management strategies is essential.
To recap, the Security Risk Management Lifecycle consists of several key stages:
Asset inventory: Begin by creating a comprehensive inventory of your IT assets, including hardware, software, and data. This inventory serves as the foundation for understanding your organization’s IT infrastructure and identifying areas of potential vulnerability.
Risk identification: Identify potential risks to your IT assets by considering various vulnerabilities, threats, and attack vectors. Both internal and external sources of risk should be considered, such as employee behavior, third-party vendors, and environmental factors.
Risk assessment: Assess each identified risk based on its likelihood of occurrence and the potential impact on your organization’s IT infrastructure. This assessment will enable you to prioritize risks and allocate resources effectively to address the most significant threats.
Risk mitigation: Develop and implement targeted risk mitigation strategies to address the identified risks. This may involve applying security controls, updating software, implementing incident response plans, or adjusting business processes. Balance proactive and reactive measures to ensure comprehensive protection against current and emerging threats.
Risk monitoring and review: Continuously monitor the effectiveness of your implemented risk mitigation strategies and adjust them as necessary to address new or evolving risks. Regularly review risk assessments and update your organization’s risk profile to maintain an accurate and up-to-date understanding of your IT security landscape.
In addition to implementing the Security Risk Management Lifecycle, it is vital to consider department-specific risk management activities. By conducting department-specific risk assessments, providing customized security awareness training, developing incident response plans for each department, and monitoring and reporting the effectiveness of these activities, you can ensure a secure environment across your entire organization.
Moreover, don’t forget about the importance of information system security to risk management and activities. Securing your organization’s information systems and ensuring critical data confidentiality, integrity, and availability should be top priorities.
Conduct system-specific risk assessments, implement appropriate security controls, harden information systems, and continuously monitor these systems for signs of potential security incidents.
Lastly, consider implementing security control profiles to streamline your risk management activities and ensure compliance with relevant regulations and industry standards.
Examples of security control profiles include PCI DSS, HIPAA Security Rule, NIST Cybersecurity Framework, and ISO/IEC 27001. By adopting these predefined sets of security controls, your organization can efficiently address specific risks, regulatory requirements, or industry standards.
As you work towards mastering the Security Risk Management Lifecycle, remember that maintaining a strong IT security posture is an ongoing process that requires constant vigilance, adaptation, and improvement.
Staying informed about emerging threats and best security practices, investing in employee training, and continuously refining your risk management processes, you’ll be well-equipped to protect your organization from potential threats and ensure its sustained growth and success in an increasingly connected world.
The Security Risk Management Lifecycle is essential to any organization’s cybersecurity strategy. Organizations can better protect their digital assets, maintain business continuity, and safeguard their reputation.
Adopting the Integrated Adaptive Management Model (IAMM) and implementing effective risk management processes.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.