Cyber security is more important than ever in today’s digital age. With the rise of online shopping, social media, and Cloud-based services, businesses and individuals are increasingly vulnerable to cyber-attacks.
That’s why it’s so important to have a solid cybersecurity risk management framework in place. The average cost of cyberattacks now exceeds $1.1m, and 37% of companies were affected after the attacks.
A cyber security risk management framework is a set of guidelines and best practices for managing cyber security risks. Risk management cyber security is designed to help organizations identify, assess, and mitigate risks associated with their use of technology.
A cyber security risk management framework aims to protect an organization’s information assets from unauthorized access, use, disclosure, or destruction. An organization must have a cyber risk management strategy to counter cyber risks.
Many different cyber security risk management frameworks are available, but they all share certain common elements. These elements include:
- Identifying the organization’s assets and data that are most at risk from cybersecurity threats;
- Understanding the types of cybersecurity threats that could pose a risk to these assets and data;
- Assessing the likelihood and potential impact of these threats;
- Selecting appropriate controls to mitigate the risks;
- Implementing these controls; and
- Monitoring and testing the effectiveness of the controls on an ongoing basis.
An effective cyber security risk management framework will be tailored to the organization’s specific needs. It should be updated regularly to reflect changes in the organization’s assets, data, and business operations and changes in the cybersecurity threat landscape.
There are many reasons why a cyber security risk management framework is so important. First and foremost, it helps organizations to protect their most valuable asset—their data. In addition, it helps to ensure compliance with industry regulations and standards, such as the General Data Protection Regulation (GDPR). Finally, it can help organizations avoid major financial losses in a successful cyber attack.
There are many different ways to create a cyber security risk management framework. One common approach is known as the NIST Cybersecurity Framework (NCSF). The NCSF was developed by the National Institute of Standards and Technology (NIST), and it guides how organizations can manage their cybersecurity risks.
Another popular approach is known as the ISO 27001 standard. ISO 27001 is an international standard that guides on developing, implementing, and maintaining an effective information security management system (ISMS).
As companies increasingly rely on technology to conduct business, cyber-attacks risk has become a greater concern. A comprehensive cyber security risk management framework can help organizations identify and assess their risks and develop mitigation strategies. This blog post will discuss the key components of such a framework and provide some tips for implementing it. Thanks for reading!
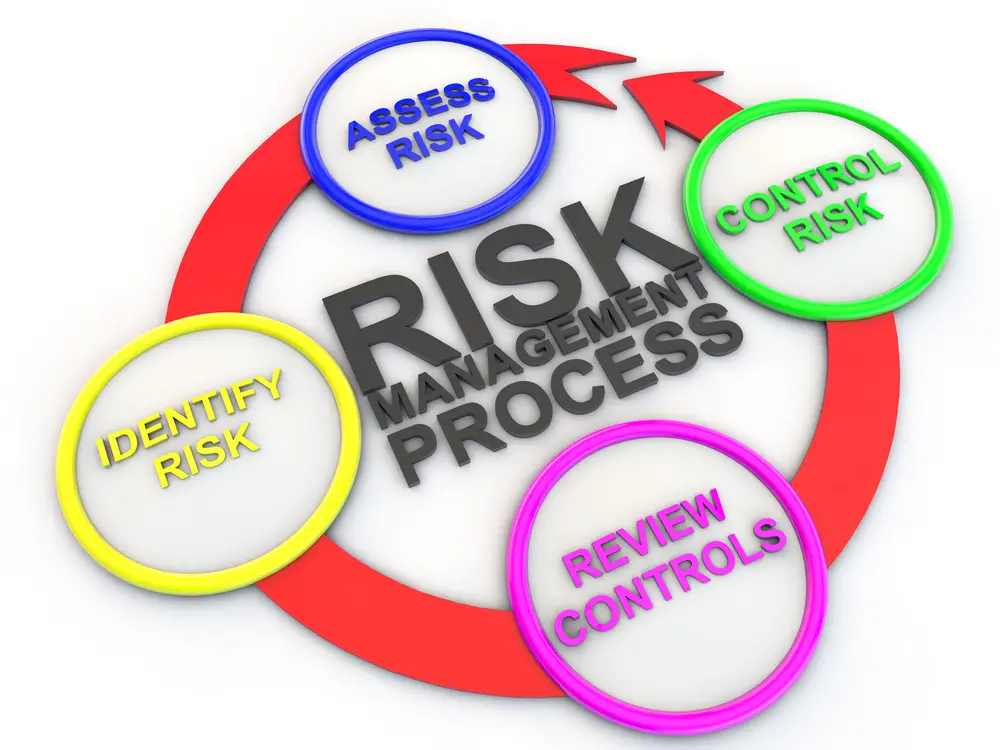
What is cyber security risk management?
Cybersecurity risk management involves determining priorities for threats. Organizations use cybersecurity risk management to ensure critical security threats are dealt with quickly and effectively.
This method assists in understanding threats by identifying their potential effects. Risk management understands how organizations can eliminate all system vulnerabilities and stop cyber attacks.
In addition to addressing cybersecurity risks, organizations must address critical threats to avoid the occurrence of vulnerabilities.
What is a cyber security risk assessment?
The cybersecurity risks assessment process assists organizations in the identification of business goals and the appropriate IT assets needed for achieving those goals. It involves the identification of malicious cyberattacks affecting this IT asset.
The organization should determine the likelihood that such attacks could occur and must also determine the potential impact. The cybersecurity risk assessment is meant for organizations that need help identifying threats that can affect their business goals in the organization.
Cybersecurity Risk Management Process
When evaluating risks, companies typically use four steps that begin with the identification of risks to manage the risk. Next, a risk assessment is performed on potential threats, utilizing vulnerability and its potential effects. Typically risk is rated prioritizing by organizations, and the company can choose from many mitigation plans. The fourth steps is to monitor risk and control current despite constantly shifting environments.
- Identify risks- identify where there may be risks in the enterprise.
- Risk assessment – The risk of a vulnerability will be weighed on its possible consequences. Identify risks in order of severity.
- Monitor risk – Risks are constantly monitored and have an integrated risk management plan that evolves to reflect changing environments in organizations. Security risks can be easily identified and managed using a robust security plan that provides the necessary security controls for the organization.
Cyber Risk Management Frameworks
Several frameworks for cyber security management provide standards organizations could use. The Cyber Risk Management framework provides an integrated approach for organizations in identifying and assessing mitigated risks, managing them, and identifying procedures for addressing security risks.
In addition to NIST SP 800-53, several other security standards include good practice guidelines regarding cyber threats. The ISO 22702 Security Risk Assessment (ISRFA) contains 108 recommended cybersecurity activities for five critical security functions: identification, protection, detection, response, and recovery.

Types of cybersecurity risk management frameworks
The framework provides standards to enable security leaders across all industries and sectors to know what their security posture is today. A framework makes identifying risk management activities much easier.
ISO
ISO 270001 is ISO’s longest-standing cybersecurity framework. Using these frameworks, the organization provides standardized guidelines and procedures to manage systematically the risks a data system may pose. It maintains ISO 33010, which defines the principles that guide effective enterprise risk management.
International Organization for Standardization (ISO) – Is ISO270001 an ISO standard? ISO/IEC 27001 provides security guidelines for managing risks from information technology systems. Organizations may use ISO 31000 Standard, which provides guidelines to manage business risks. This is an appropriate technology cybersecurity framework.
DoD RMF
The Department of Security – Cybersecurity Management Framework (SSMF) guide managing the cyber security risk across, e.g., IT assets. From here, the RMMF divides its cyber security plan into six steps: classification, implementation assessment, and authorization monitoring.
NIST CSF
NIST’s cyber-security framework is a well-known framework. The Framework is aimed at standardizing risk management. NIST. The report defines activities related to the key functions of cyber-risk management: protection and recovery of data, identifying, responding, and recovering data. The NIST cyber risk management approach is a great risk management initiative that combines risks and cybersecurity.
FAIR Framework
The Framework aims to provide information risk assessment and analysis tools that can assist enterprises in understanding, analyzing, and measuring information risks. The goal was to provide guidance and help organizations implement a more efficient cybersecurity strategy.
Best practices for cybersecurity risk management
It is important to understand how to manage cybersecurity risk effectively.
Be attentive to your threat environment
Cybercriminals have used social networking information to launch sophisticated whaling attacks. Typically, whaling attacks target senior managers (CEOs and CFOs) to get company information.
Hackers disguise themselves to gain access to financial or personal details by pretending to be CEOs or other executives. This is why companies should consider hiring cybersecurity experts. They can provide them with an opportunity to develop their own knowledge in the field.
Encourage diverse views
Too often, cybersecurity staff or management view risks from one point of view. Cybercriminals can often look “out of the box” and identify vulnerabilities you’ll never even know existed.
Therefore, it helps encourage team members to think about different viewpoints through penetration tests and simulations. Testing allows workers to see what hacking is doing to help identify potential threats or mitigate them.
Train employees
Employee training should help create security awareness and help employees understand how security systems and tools are used. Ideally, staff should receive comprehensive training in identifying and reducing identified risks. To protect against such attacks, human employees must know what type of content they should not share via email or who they can contact. This is essential in developing a secure organizational culture.
Develop a risk assessment process
A cybersecurity risk analysis is a crucial aspect of planning for cybersecurity. It’s important: Find out what digital assets you’ve created for your business. Identify any possible cyber threats, external (hacking attacks, ransomware, and many other types of malicious malware) and internal. Tell me a financial or another impact that would occur in a theft or loss of property. List the probability that a possible danger occurs.
Incident response plan
Develop incident response plans that emphasize your risk prioritizing the risk identified earlier. You must find out what must be done if the threat is discovered. It should include a detailed plan that lets the team know when to react if a particular incident occurs.
Build a company culture
It is important for companies to think carefully about their culture when developing cybersecurity programs. The average cost of cyberattacks now exceeds $1.1m, and 37% of companies were affected after the attacks. You need a cyber security culture across your entire organization.

Implement a cybersecurity framework
You should use appropriate security frameworks. Normally, this varies depending on your industry s standard. The most commonly adopted cybersecurity standards are PCI DSS ISO 27001.
Develop a Cybersecurity Risk Management Plan
Identify Cybersecurity Risks
Using Gartner’s definition of IT risk, the company refers to a potential unanticipated business impact that may result from a failed IT infrastructure. Is there any risk of exploiting existing vulnerabilities? Risk identification is a part of the management process. Modern security managers are battling the growing complexity created by COVID, resulting in risks around each corner. If we are looking to identify risk, it’s essential for us to know how to deal proactively and correctly with these issues.
Assess cyber security risks
Risk assessments provide a perfect opportunity to highlight security across your organization. Assessing risks allows your organization to practice communication and collaboration as key components of future risk management. Can you list the risks to your organization? Assessments are important steps in the right direction if the answers are clear. Start identifying assets as important as possible. Secondly, identify potential threats and vulnerabilities in the environment through information security risk criteria.
Identify Cybersecurity Risk Mitigation Measures
Identification and assessment of risk begin. How should your company handle this risk? How do you respond to risks? Tell me a way of managing residual risks. History shows that risk management teams have an effective risk response strategy in place. It’s the third and simplest stage of responding to threats. The technology aims to reduce technological risk by employing encryption and firewalling tools.
Use Continuous monitoring
Your organization is assessing risks in your environment. It’d be good. However, change can be unpredictable, and the organization should monitor environments to ensure internal controls are in sync with IT risks. You should keep track of the changes that affect your organization, ensuring you maintain internal controls that conform with external expectations. Veneer Risk- Always check your security measures and documentation before adding vendors on board. Remember that these flaws will cause headaches.

Conclusion
A cyber security risk management framework is essential for any organization that wants to protect its data assets from unauthorized access or destruction. Using a Framework, organizations can ensure compliance with industry regulations, avoid major financial losses in the event of a successful cyber attack, and protect their most valuable asset—their data.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.

