Rapidly evolving digital landscape has ensured IT risk management has become a crucial component of any organization’s success.
The increasing complexity and interconnectedness of IT systems expose businesses to a wide range of risks that could lead to financial losses, reputational damage, or even operational failure.
In the digital era, IT risk management has become a critical component of organizational success. Navigating complex IT systems and ever-evolving cyber threats requires a solid risk management strategy.
Understanding the IT risk management lifecycle is essential to effectively manage and mitigate these risks. In this blog post, we will delve into the various stages of the IT risk management lifecycle, offering practical advice and insights to help you strengthen your organization’s vendor risk management lifecycle strategy.

What is the Planning Phase of the Risk Management Life Cycle?
During the planning stages, the risks are analyzed and evaluated to determination of a way to implement the work. Understanding risk management cycles can help you identify potential adverse impacts on projects or outcomes.
The planning phase includes assessing risks, probability, impact analysis, and planning. Identify potential risks and determine the appropriate response. Depending on the risk a person faces, a plan will develop or allocate money to address an eventual problem.
Key Components of a Risk Management Lifecycle
Most risk management organizations are generally convinced that life cycle processes contain a range of processes.
The risk owner is responsible for determining his/her management of risk. This action does not carry any risk. Any process for managing risks must operate within ‘rewards’ within an ‘environmental framework’.
Monitor and control strategies
Monitoring and controlling strategies are essential components of effective risk management, project management, and business operations.
These processes involve tracking the progress of strategic initiatives, evaluating their performance, and taking corrective actions when necessary to ensure that objectives are met.
Develop Key Performance Indicators (KPIs)
Identify relevant KPIs that align with your strategic objectives and provide measurable insights into the progress and success of your initiatives.
KPIs should be specific, achievable, and time-bound, allowing you to track performance and make data-driven decisions.
Establish a Monitoring and Control System
Create a system to regularly collect, analyze, and report data related to your KPIs. This system should provide real-time information on the performance of your initiatives, enabling you to identify trends, spot potential issues, and take timely corrective actions.
Set Performance Targets and Thresholds
Determine performance targets for each KPI, and establish thresholds that indicate when performance is off-track or requires corrective action.
The targets and thresholds serve as benchmarks against which you can measure the progress of your initiatives and determine the need for adjustments.
Schedule Regular Reviews
Conduct periodic reviews of your initiatives’ performance to assess progress towards your objectives and identify areas for improvement. These reviews should involve relevant stakeholders, such as team members, the project management institute, managers, and senior leaders, to ensure that multiple perspectives are considered.
Implement Corrective Actions
When monitoring and control processes reveal deviations from your performance targets or other issues, implement corrective actions to get your initiatives back on track. These actions may include adjusting resources, revising timelines, or modifying strategies as needed
Leverage Technology
Utilize technology, such as project management software, business intelligence tools, or data visualization platforms, to support your monitoring and control efforts.
These tools can help automate data collection, analysis, and reporting, providing you with timely and accurate insights to inform your decision-making.
Risk response
Risk response is the process of developing and implementing strategies to address identified risks in a project or business context.
The goal of risk response is to minimize the likelihood or impact of adverse events while maximizing opportunities for positive outcomes.
There are four primary risk response strategies, each suited to different types of risks:
Risk avoidance is most suitable for high-impact risks that cannot be effectively mitigated or transferred. Examples include canceling a project with significant uncertainties or choosing not to enter a high-risk market.
Risk Mitigation: Risk mitigation focuses on reducing the likelihood or impact of a risk event through proactive measures. This strategy can involve implementing additional controls, improving processes, or investing in new technology.
For example, a company might invest in cybersecurity measures to reduce the likelihood of a data breach or develop a backup plan to minimize the impact of supply chain disruptions.
Risk Transfer: This strategy involves shifting the risk to a third party, usually by means of insurance, contracts, or partnerships. Risk transfer is most appropriate for risks that can be effectively managed by external parties or for which the potential impact is too significant for the organization to bear alone.
Examples include purchasing insurance to cover potential losses from natural disasters or outsourcing a complex project component to a specialized vendor.
Risk Acceptance: In some cases, an organization may decide to accept a risk if the potential benefits outweigh the potential consequences, or if other response strategies are not feasible or cost-effective.
Risk acceptance involves acknowledging the risk and being prepared to manage its consequences should the risk event occur. For example, a company might accept the risk of fluctuating currency exchange rates and develop contingency plans to address potential financial impacts.
It’s essential to choose the appropriate risk response strategy based on the specific risk’s nature, potential impact, and likelihood. In some cases, organizations may need to use a combination of strategies to address a single risk effectively.

Managing risks throughout the project lifecycle
A proactive approach to risk management helps identify potential issues early, allowing for the implementation of appropriate mitigation strategies.
Initiating Phase:
During the project initiation phase, establish the risk management context by considering the project’s goals, scope, stakeholders, and potential constraints.
Identify high-level risks that could impact the project’s success and prioritize them based on their potential impact and likelihood.
Planning Phase:
Develop a comprehensive risk management plan as part of the overall project plan. This includes defining risk management roles and responsibilities, evaluate risk,, selecting risk assessment methodologies, and setting risk management procedures and guidelines.
Ensure that risk management activities are integrated into other project planning processes, such as schedule development and resource planning.
Risk Identification:
At the beginning of the project and throughout its lifecycle, continuously identify potential risks that could impact the the project manager’s objectives.
Use various risk identification techniques, such as brainstorming, historical data analysis, and stakeholder interviews, to ensure a comprehensive understanding of potential risks.
Risk Assessment:
Evaluate the identified risks by assessing their likelihood of occurrence and potential impact on the project. Use qualitative or quantitative methods to prioritize risks and develop a risk register to document and track them.
Risk Response Planning:
Develop risk response strategies for prioritized risks, including risk avoidance, mitigation, transfer, or acceptance.
Involve relevant stakeholders in the risk exposure and decision-making process and integrate risk responses into the overall project plan.
Risk Monitoring and Control:
Throughout the project and risk lifecycle however, continuously monitor and control risks by tracking their status, assessing the effectiveness of risk response strategies, and implementing necessary adjustments.
Regularly report on risk management activities to keep key stakeholders informed and maintain a proactive approach to risk management.
Risk Management Framework
A strong risk management framework is essential for organizations to navigate the complex and evolving landscape of risks. Be proactive in identifying, assessing, and mitigating risks, organizations can safeguard their assets, reputation, and long-term success.
Establish the Risk Management Context
Begin business process by defining the scope, objectives, and priorities of your risk management efforts. Align them with your organization’s strategic goals, legal and regulatory requirements, industry standards, and stakeholder expectations. This step ensures that your risk management framework is relevant and tailored to your organization’s specific context.
Develop a Risk Management Policy
Formulate a clear and concise risk management policy that outlines your organization’s approach to managing risks. The policy should include principles and guidelines, risk appetite and tolerance levels, and the roles and responsibilities of various stakeholders in the risk management process.
Assemble a Risk Management Team
Create a cross-functional vendor risk management team that represents key areas of your organization, such as IT, finance, operations, and human resources. This team will be responsible for overseeing the implementation, monitoring, and continuous improvement of the risk management framework.
Adopt Risk Assessment Methodologies
Select appropriate risk assessment methodologies based on your organization’s needs and the types of risks you face. These methodologies could include qualitative or quantitative analysis, scenario analysis, or expert judgment. Ensure that your chosen methods are consistent, transparent, and widely understood.
Implement Risk Mitigation Strategies
Develop risk mitigation strategies to address identified risks. These strategies should be based on the risk priorities determined during the risk assessment process and may include risk avoidance, risk reduction, risk transfer, or risk acceptance. Create an action plan for implementing these strategies and assign responsibilities to relevant team members.
Establish Risk Monitoring and Reporting Mechanisms
Set up a system to continuously monitor the effectiveness of your risk management efforts. Develop key performance indicators (KPIs) to measure the success of risk mitigation strategies and conduct regular audits and risk assessments, to verify the effectiveness of risk controls. Establish a clear reporting structure and schedule to ensure that risk-related information is communicated effectively to all relevant stakeholders.
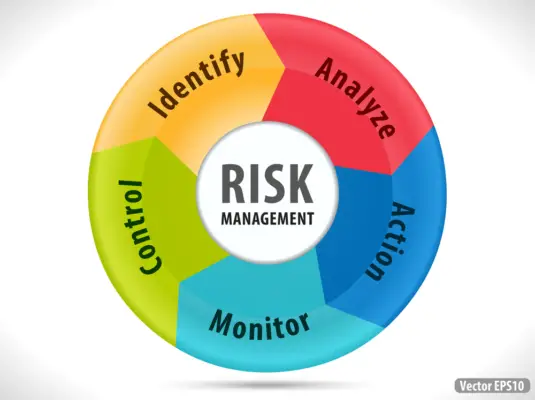
Risk Identification(Identifying risks)
The first step in the IT risk management lifecycle is to identify the potential risks that your organization faces. This involves evaluating your organization’s IT infrastructure, processes, and human resources to uncover vulnerabilities, threats, and potential risk events.
Key considerations in risk identification:
- Assess internal and external threats, such as cybersecurity attacks, system failures, natural disasters, and human errors.
- Review existing policies, procedures, and controls to identify gaps in risk mitigation.
- Conduct a comprehensive inventory of your IT assets, including hardware, software, and data.
- Consult with stakeholders, including employees, vendors, and customers, to gather their perspectives on potential risks.
Risk Assessment(Assessing their impact)
Once you have identified the risks, the next step is to categorize risks and assess their impact on your organization. This involves estimating the probability of a risk event occurring and evaluating the potential consequences if it does.
Key aspects of risk assessment:
- Develop a risk matrix to prioritize risks based on their impact and likelihood.
- Use quantitative methods, such as financial modeling, to estimate potential losses.
- Employ qualitative techniques, such as expert opinions, to assess the intangible effects of risks on your organization’s reputation and stakeholder relationships.
Risk Mitigation(Defining risk control strategies)
Risk mitigation focuses on developing strategies to reduce the likelihood of risk events occurring or minimize their impact if they do. This could involve implementing new policies, procedures, or technologies, or updating existing ones.
Key elements of risk mitigation:
- Choose appropriate mitigation techniques, such as risk avoidance, risk transfer, risk reduction, or risk acceptance.
- Create an action plan that outlines the steps required to implement each mitigation strategy.
- Assign responsibilities to specific team members for implementing and monitoring mitigation efforts.
- Communicate mitigation strategies to all relevant stakeholders.
Risk Monitoring(Monitoring and Review)
Continuous monitoring is crucial to ensuring the effectiveness of your risk management strategy. Regularly track and review the progress of risk mitigation efforts to identify areas for improvement and make necessary adjustments.
Key components of risk monitoring:
- Develop key performance indicators (KPIs) to measure the success of risk mitigation efforts.
- Conduct regular audits and assessments to verify the effectiveness of risk controls.
- Monitor changes in the internal and external environment that could affect your organization’s risk profile.
- Establish a feedback loop with stakeholders to gather their input on risk management efforts.
Risk Reporting(Reporting the results)
Effective risk communication is essential for maintaining transparency and accountability within your organization. Regularly report on the status of risk management efforts to stakeholders, including senior management, employees, and regulatory authorities.
Key elements of risk reporting:
- Develop a risk reporting template that captures essential information, such as risk priorities, mitigation actions, and progress updates.
- Ensure that reports are clear, concise, and tailored to the needs of different stakeholder groups.
- Establish a schedule for regular risk reporting, such as quarterly or annually.
- Utilize visual aids, such as graphs and charts, to effectively communicate complex risk data.
Risk management process by life cycle phase – Risk Assessment and Quality Project Management
Continuous Improvement
As the digital landscape continues to evolve, it’s essential to adapt your IT risk management strategy accordingly. Embrace a culture of continuous improvement to ensure that your risk management efforts remain effective and relevant.
Key steps in continuous improvement:
- Review and update your risk management policies and procedures regularly to reflect changes in technology, regulations, and industry best practices.
- Encourage open communication and feedback among stakeholders to identify areas for improvement.
- Invest in employee training and development to build a skilled and risk-aware workforce.
- Utilize emerging technologies, such as artificial intelligence and machine learning, to enhance your risk management capabilities.
Regulatory Compliance
In many industries, regulatory compliance is a critical aspect of IT risk management. Ensure that your organization adheres to relevant laws, regulations, and industry standards to avoid fines, penalties, or reputational damage.
Key aspects of regulatory compliance:
- Stay informed about changes in applicable regulations and industry standards.
- Conduct regular compliance audits to identify and address gaps in your risk management strategy.
- Collaborate with legal and regulatory experts to ensure that your organization’s risk management efforts meet compliance requirements.
- Develop a compliance management system to streamline the process of identifying, managing, and reporting on regulatory risks.
Building a Risk-Aware Culture
An organization’s success in managing IT risks depends on its ability to foster a risk-aware culture. Encourage employees at all levels to actively participate in risk management efforts and to understand their role in maintaining a secure and resilient IT environment.
Key strategies for building a risk-aware culture:
- Provide regular training and educational opportunities to keep employees informed about risk management best practices and their responsibilities.
- Recognize and reward employees who proactively identify and address risks or contribute to risk management efforts.
- Incorporate risk management objectives into performance evaluations and goal-setting processes.
- Promote open communication and collaboration among departments and teams to facilitate the sharing of risk-related information and insights.
Through diligent following the IT risk management lifecycle and integrating risk management into your organization’s culture, you can create a resilient, secure, and successful organization that is well-equipped to navigate the ever-changing digital landscape.

Conclusion
Managing IT risks is a continuous and dynamic process that requires constant vigilance and adaptation. By understanding and following the IT risk management lifecycle, you can help your organization proactively identify, assess, mitigate, monitor, and report on risks to ensure the ongoing success and resilience of your business.
Implementing a robust IT risk management strategy not only protects your organization from potential threats but also fosters a culture of risk awareness and preparedness. By taking a proactive approach to risk management, you can enhance your organization’s agility, competitiveness, and overall performance.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.

