A vendor risk management program is a process by which your organization identifies, assesses, and manages the risks associated with doing business with third-party vendors. Such a program is essential for two reasons: first, it helps protect your organization from potential harm. And second, it can help improve your organization’s overall risk posture by identifying and mitigating potential vulnerabilities.
The blog post will show the various steps involved in setting up a successful vendor risk management program. When setting up a vendor risk management program, first understand the organization’s overall risk posture. It means understanding the risks associated with the organization’s core business functions and the risks associated with its interactions with third-party vendors.
Managing risks is crucial to building successful companies. Managing vendor risk is critical for companies as global connectivity and supply chains expand globally. Develop a risk management strategy to determine risks and minimize those risks, including addressing various areas, including cyber security, regulatory compliance, vendor relationships, and risk management.
The above areas need addressing from the company and vendor sides to mitigate risk. Cybersecurity threats are ever-growing and evolving, so companies have a robust strategy in place that includes vendor risk management. Regulations are also constantly changing, so compliance must be managed on an ongoing basis. Relationship risks with vendors can also lead to security breaches and financial losses, so managing those relationships is essential.
Depending on the size and scope of the organization, outsourcing tasks might be essential. Regardless of the source of materials you use, third parties can help you develop a strong relationship with your growing business. Using the internet can be helpful. This new risk also puts your company at risk. How do I check my vendors’ compliance? Vendor risks management (VRM) is focused on managing third-party risks.
High risk vendors based on vendor performance and third party risk assessment. Third party relationships are crucial in risk assessments.
Finally, having a risk management strategy in place will help your company make better decisions regarding mitigating risk. It is a tool in today’s highly connected and globalized world.
What is Vendor Risk Management? Understanding VRM
Vendor Risk Management (VRM) is a risk management discipline to identify the potential risk related to vendors. Managing compliance and risk management helps organizations identify vendor relationships and the extent and effectiveness of the protection measures.
As a discipline, VRM is under rapid evolution. Every day a vendor faces new business continuity and privacy issues that affect customers. Digital transformation relies increasingly on vendors (mainly cloud-based providers), becoming a Board concern.
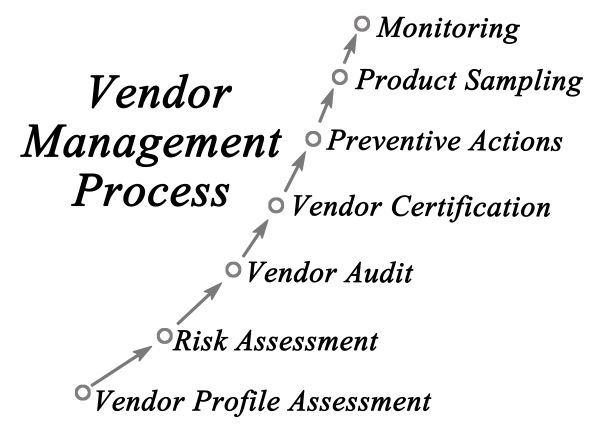
Risk Management process
A strategic VRM program can be a critical part of a company’s risk management system if needed. ERM uses the concept of VRM — an effective strategy to assess risk — in the context of a business proactively. This risk management strategy involves investing in the best quality tools and products and purchasing insurance to help cover natural and artificial catastrophes.
Risk sensitivity and management are equally for the health and longevity of modern companies within the global economy. A proactive ERM program is one of the best ways to protect your business from potential risks and minimize any negative impact on your company.
It’s important to note that a comprehensive ERM program goes beyond insurance coverage and risk assessment tools. A successful ERM strategy requires commitment from the entire organization, including top management. The goal is to create a risk-aware culture where risk is managed at all levels.
Implementing an ERM program can be a complex process, but the benefits make it well worth the effort. By taking a proactive approach to risk management, you can protect your business from potential losses and maintain a solid competitive edge.
The vendor risk assessment process follows the risk assessment methodology inherent in the organization’s risk management process. The vendor risk management process that deals with vendor management are included in thirty party risk. The risk exposure is inherent in data security risks.
What is Vendor Relationship Management?
When evaluating an enterprise software company, you must determine how their business fits into their overall project. Third-party relations can be from small projects with a single contractor to ongoing vendor relations with a multinational. Typically a vendor is responsible for coordinating all vendor relationships and ensuring they have the correct information and services for the delivery and management of a business. It is called vendor management.
Benefits of Vendor Risk Management
Investing in VRM gives you confidence. If your due diligence has been completed, you can focus on your work instead of taking care of your contractors. The freedom of choice gives you the ability to develop an organization and find opportunities as they emerge. Increasing your communication skills will improve your products and services quality. As long as everyone walks on guard, there is easy for the company and your customers. VRM can help protect your organization from future breaches by minimizing your risk exposure.
- Proactively manage and mitigate risk associated with doing business with third-party vendors.
- Mitigate the impact of supplier failures on your organization.
- Protect your company’s data and reputation.
- Gain visibility into your supply chain and better assess risks.
- Reduce costs associated with managing supplier risk
Importance of Vendor Risk Management
Increasingly, firms outsource critical tasks to suppliers, resulting in heightened costs and benefits. Although working with an agency can make a massive difference for the company, the risks are also high. Recent incidents, including Covid-19 Pandemics, SolarWind’s attacks on SolarWind, and other ransomware breaches, have highlighted vendors’ risks. This event affected millions of businesses – no matter industry size or country.
- Vendor risk management helps protect an organization from potential harm its vendors could cause. There are three main types of risks that vendors can cause: financial, operational, and compliance.
- Vendor risk management helps mitigate these risks by establishing procedures and policies for managing vendor relationships. It is essential to understand the organization’s risk appetite clearly to determine which risks are acceptable and which ones need to be mitigated.
- The goal of vendor risk management is to ensure that the organization can continue to do business with its vendors while minimizing the risk of any potential harm.
What is a Vendor Risk Management Program?
Vendor risk management (VRM) is an approach to assess whether services or IT providers are creating unwelcome potential problems. The goal of VRM is to protect the organization by reducing or eliminating these risks. The first step in VRM is understanding the different types of risks that vendors can pose.
There are three general types of risks that vendors can pose: business, technical, and compliance. Business risks include the vendor going out of business, not meeting performance requirements, or providing a higher price than expected.
Technical risks include the vendor’s IT infrastructure not being able to meet the organization’s security requirements or the vendor’s software not complying with the organization’s standards. Compliance risks include the vendor not adhering to privacy or data protection laws.
How Do you Create a Vendor Risk Management Program?
How can vendors manage their risk and compliance? Create governance documents appropriate for the organization. Make it clear what the vendor selection is. ‘ Set a contract standard. Maintain regular due diligence & constant monitoring.
Creating a Vendor Risk Management program can seem daunting, but following a few simple steps can make the process much easier. The first step is to create governance documents that outline the specific requirements for potential vendors. It will help narrow down the vendor selection process and ensure that only qualified companies are considered.
Once you’ve selected your vendors, set a contract standard that outlines the specific expectations and requirements for doing business with them. It will help prevent any misunderstandings down the road and ensure that both parties are held accountable.
Finally, maintain regular due diligence and constant monitoring of your vendors’ risk and compliance posture. It will help you stay ahead of any potential issues and protect your business.
Developing a Successful Vendor Risk Management Program
Risk management should first be developed in an organization’s relationship. A company must partner with IT security experts to develop a foundation for a successful risk management plan.
It is critical that you understand the ways third-party management takes on risks. To initiate the new onboarding process, the two organizations must determine the appropriate risk before any exchange of confidential information begins.
Third parties must assess the supply chain relationships and the risk management processes. They must also identify and assess the risks posed by their business processes and technology.
Once a company understands how to manage risk, it can develop a strategy for mitigating those risks. Mitigation strategies will vary depending on the type of risk. A company may need to conduct due diligence on a third party, contractually bind them to specific security requirements, or limit the type of data shared.
Best Way to Manage Vendor Risk
Those involved in the third-party business process are exposed to numerous risks. Vendors handling sensitive, confidential, or classified data for you can be very risky. You will likely run into significant issues when you have poor internal security controls on your business.
An overly cautious focus on operational risks like performance standards and KPIs doesn’t suffice. A growing number of risks are posed by third-party providers, including reputation and financial risks, such as a breach.
The providers you work with can significantly impact your ability to mitigate and manage risk. It develops a process for managing the risks associated with your providers. This process should include:
- A Risk Assessment – This should be done before selecting a provider and ongoing. The assessment should include an evaluation of the provider’s risk to your organization and how you plan to mitigate that risk.
- Contracting Processes – The contracting process should include specific clauses related to risk management.
- Oversight Processes – You need to have processes in place for ongoing monitoring of the provider’s performance and compliance with the contract.
Developing a process for managing the risks associated with your providers is critical to protecting your organization. By taking the time to do this, you can minimize the risks of hurting your business.
What is a Vendor Risk Management Plan?
A vendor risk management plan is a broad initiative describing behaviour, service level access, and access to the business and potential vendors. It will be helpful for both the organizations and third parties. This document will outline what organizations can do to ensure the vendor’s performance.
The report should describe what helps the vendor maintain regulatory compliance and protect customers’ personal information from unauthorized use. Depending on supplier or service providers, relationships can be explained by step, with a checklist, or informal.
An effective plan will help manage and contain the risk related to a business relationship. It should be designed to answer the key questions that can arise from any third-party connection. The goal is to protect both the customer and the vendor by maintaining an open and communicative relationship.

Role of third party vendors
Third-party vendors are virtually anybody providing services for your organization who has no job for you in that organization.
- Third-party vendors can play a role in helping businesses to reach new customers and grow their business.
- Businesses should carefully consider the benefits and drawbacks of working with third-party vendors before entering into a partnership.
- Third-party vendors can help businesses save time and money, but there is also a risk that businesses could lose control over their data or be exposed to security risks.
- Businesses should take steps to protect their data and ensure that they are comfortable with the security measures that third-party vendors have in place.
What is Vendor Lifecycle Management?
It is generally the customer relationship lifecycle. For highly risky vendors, steps might be skipped or even lead to the early termination of contracts. Vendor Lifecycle Management is the term given to the ongoing management of a vendor relationship. It includes initial selection, onboarding, management of performance, contract renewal, or termination.
The main aim of Vendor Lifecycle Management is to ensure that the vendor relationship is productive and meets the customer’s needs. It is not a one-time process but instead needs to be continually managed to get the best results.
Vendor Risk Management Lifecycle
The vendor risk management lifecycle describes the process that develops with vendors over the years. In some cases, VRM is also known as vendor relations management, describing a business engagement in a relationship. The VRM life cycle comprises the following sections. What’s the best method for conducting vendor risk assessments?
Vendor Risk Assessment (also referred to as third parties) is a survey used by firms to assess the risks they face. Many companies use outside services to help with the assessment. The main aim is to identify and assess potential threats before they become a problem.
Risks can come from several sources, including the vendor’s financial stability, ability to meet security requirements, and compliance with laws and regulations.
Vendor Risk Management Tools
The software improves vendor risk management in many ways. The software helps identify the best possible risks and improve operational efficiency. Traditional security questionnaires and testing are very costly and often hinder your understanding of the digital supply chain’s security postures.
The delay will significantly increase your risk and may negatively impact business results by preventing you from informing your new suppliers. Consider acquiring software that will help your organization evaluate supplier information more accurately and efficiently.
The goal of automating vendor risk management is to improve the accuracy and efficiency of the process. Automation can help identify the best possible risks and improve operational efficiency. It also allows you better to understand the digital supply chain’s security posture. The delay will significantly increase your risk and may negatively impact business results.
Consider acquiring software that will help your organization evaluate supplier information more accurately and efficiently. When deciding on automating vendor risk management, weigh the benefits against the costs. The goal should be to improve the accuracy and efficiency of the process, but this may not always be possible or practical.
How Can ZenGRC Help You?
ZenGRC helps you track risks in your business and provides tools to various vendors. Automation will make sending surveys to your customers more accessible and show you the best strategy that your company should take if it wants to prevent threats.
Vendor Risk Management Best Practices
Best Practices on vendor risk management: Keeping a good practice in mind is not worth putting into practice. Generally, vendors breach rules and protocols by not implementing them. Both vendors must communicate in transparent terms the risks they are facing.

Tell me the best way to deal with a vendor breach?
It’s not easy to ensure your organization’s website is secured anymore. You should be able to take into account the risk of third parties and other third parties. Your suppliers may become targets for cybercriminals or accidentally reveal confidential information through improper configuration.
Delays on schedules, failure to deliver contracts, or cuts can be disastrous financially or reputationally, but they can also cause your business a loss of revenue and profits. With a vendor-specific risk management system, the business can act quickly on breaches.
How do I create a third party risk management checklist?
When you’re planning to hire new vendors, it should be easy for you to check that they meet their requirements—often called vendor assessment. The critical components for a vendor assessment will be identified and done. You could also try implementing software automating vendor evaluation questionnaires.
Minimize Vendor Risk for Maximum Performance and Profits
It is impossible to control our world, but it’s possible. With the help of an innovative risk management software program, you can improve the quality and productivity of the product, production, and public reputation you need to anticipate and mitigate risk. In the business world, that’s what we call risk management. To make money and protect our businesses, we need to ensure disruptions and malfunctions don’t happen.
How do You Implement Vendor Risk Management Programs?
Implementing a VRM program will depend significantly on the size of your business or the size of your supplier management program.
- Work with vendors to develop a risk management program specific to your organization.
- Define the types of risks each vendor poses to your organization.
- Assess the likelihood and impact of a security incident involving each vendor.
- Mitigate risks by implementing security controls and contractual protections.
- Periodically review and update your risk management program.
How Do Companies Manage Vendor Risk?
It is not possible to handle all vendor risks in the same fashion. All businesses are unique. Businesses to implement effective VRM programs. Measures entail:
- Establishing a clear understanding of the organization’s risk appetite and tolerance.
- Determining which risks are most important to the company must be managed proactively.
- Developing a process for assessing and managing risk, including ongoing monitoring of key indicators.
- Creating a risk management plan that includes specific actions to be taken in the event of a breach or other incident.
- Training employees on the organization’s risk management processes and identifying and responding to risks.
- Monitoring and reviewing the risk management program’s effectiveness on an ongoing basis.
Conclusion
Vendor risk management is a critical part of any company’s risk management program. By understanding what VRM is and implementing an effective VRM program, companies can protect themselves from the risks associated with doing business with third-party vendors. While there are many benefits to implementing a successful vendor risk management program, perhaps the most benefit is that it helps organizations manage their overall risk exposure.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.