Third-party risk, or vendor risk, refers to the potential threats an organization faces when it outsources aspects of its business to external companies. These threats can affect various parts of a company’s operations, including its financial performance, data security, reputation, and regulatory compliance.
The third-party risks typically include:
Operational Risk: This can result from a third party failing to deliver a product or service on time or up to the required standard. For example, a supplier failing to deliver a key component could disrupt a company’s production line.
Financial Risk: This can occur if a third party faces financial difficulties, potentially resulting in them increasing prices or even going out of business.
Cybersecurity Risk: If a third party has access to an organization’s systems or data, there’s a risk they could suffer a data breach, which could result in sensitive information being stolen.
Legal and Compliance Risk: A third party failing to comply with laws or regulations could have legal or regulatory implications for the organization that hired them.
Reputational Risk: This can occur if a third party behaves in a way that could damage an organization’s reputation. This could be due to poor service, unethical practices, or other negative actions.
To manage these risks, companies usually have a Third-Party Risk Management (TPRM) program in place, which includes a thorough vetting process before engaging with a third party and continuous monitoring and evaluation of third-party performance and risks throughout the relationship.
This helps to ensure that third parties meet their obligations and adhere to the same standards of conduct as the hiring organization.
Third-party risk is critical for organizations in today’s interconnected business environment. It refers to the potential risks when a company engages with third parties, such as vendors, suppliers, contractors, or partners.
As businesses increasingly rely on third-party relationships to deliver products and services, they expose themselves to risks that can significantly impact their operations or reputation.
Understanding third-party risk is crucial for any organization that seeks to effectively manage its business relationships and protect itself from potential threats.
This article aims to explore what third-party risk is, its impact on businesses, sources of third-party risk, and ways to mitigate them through effective vendor management practices.
Additionally, the article will outline relevant regulations and standards related to managing third-party risk that companies should comply with.

Defining Third-Party Risk
The section at hand delves into the conceptualization and explication of the multifaceted phenomena that occur when an organization engages in business partnerships with external entities.
Third-party risk refers to the potential risks arising from collaborating with an external entity, including financial, operational, legal, or reputational risks.
With the increasing trend towards outsourcing non-core functions to third parties, organizations must develop robust risk management strategies to mitigate and manage these risks effectively.
Risk assessment techniques are crucial for identifying potential threats posed by third parties.
Organizations must thoroughly analyze their partners’ activities and operations before entering contractual agreements.
This process involves evaluating factors such as their financial stability, regulatory compliance history, data security protocols, and reputation in the market.
Conducting detailed due diligence on their partners before engaging in business relationships with them, organizations can minimize exposure to potential liabilities resulting from a third party’s actions.
Effective risk management strategies must be implemented to mitigate any identified vulnerabilities adequately.
This involves setting up clear guidelines for managing relationships with third parties throughout their life cycle – from selection and onboarding through ongoing monitoring and termination if necessary.
Additionally, organizations need to establish communication channels between all stakeholders involved in these relationships to identify emerging risks and promptly implement appropriate response measures quickly.
Through these efforts, organizations can strengthen their resilience against unforeseen events by partnering with external entities without sacrificing competitive advantages or innovation possibilities.
Understanding the Impact of Third-Party Risk
One cannot underestimate the potential consequences of entrusting critical business functions to external entities, as the failure of these parties to meet expected standards can lead to significant financial losses and reputational damage.
Understanding the impact of third-party risk is an essential aspect of the risk assessment process, which involves identifying and assessing any potential risks that may arise from working with third-party vendors or partners. This means evaluating factors such as security, compliance, and operational risks.
To fully comprehend the impact of third-party risk, it is crucial to assess its consequences. The effects of a third-party failure can range from minor disruptions to critical operational failures that can result in significant financial losses or even legal action.
For instance, a data breach caused by a vendor could lead to regulatory fines and lawsuits or damage customer trust and brand reputation. Similarly, supply chain disruption caused by a supplier’s failure could cause delays in product delivery, leading to lost revenue and customer dissatisfaction.
The risk assessment process provides organizations a systematic approach to managing third-party risks effectively.
A thorough evaluation includes identifying all relevant parties involved in providing services or products, assessing their inherent risks based on factors such as industry regulations or geographic location, and evaluating their controls against established standards such as ISO 27001 or SOC 2 Type II reports.
- Third-party failures are not uncommon: Every day, there is news about companies facing severe consequences because they rely on external partners.
- Financial impacts could be devastating: TPRs have been known to cause millions, if not billions, of damage due to lost revenue streams.
- Reputational damages last long after monetary damages are paid out: The negative press associated with TPRs stays around longer than anyone would like it to.
- Recovery processes are often expensive: Companies need time (and money) dedicated solely to fixing the problem, which can detract from their overall productivity.
- No company is too small: Small businesses are just as vulnerable to the impacts of third-party risk and, in some cases, may not have the resources to recover.
Identifying Potential Sources of Third-Party Risk
Risk assessment is essential in identifying third-party risk sources since it involves evaluating the probability of occurrence and the potential impact on business operations.
To achieve optimal results, businesses can use an integrated risk management framework to provide a comprehensive understanding of their supply chain network.
One potential source of third-party risk is inadequate due diligence processes during vendor selection. Companies must perform thorough background checks before engaging any external entity to avoid associating with suppliers linked to illegal activities or those lacking compliance measures.
Other third-party risks include data breaches, cyber-attacks, regulatory violations, financial instability, and reputational damage. Risk management strategies should detect threats early enough for effective mitigation and implement preventive measures such as reviewing contracts regularly.
Additionally, geopolitical instability may pose significant risks to businesses operating across borders by exposing them to legal uncertainties or political conflicts.
Such events may lead to disruptions in supply chain networks, affecting production schedules and leading to revenue losses. Therefore, companies must have contingency plans to manage unexpected geopolitical shifts or unforeseen events.
Identifying potential sources of third-party risk requires a proactive approach toward risk assessment while implementing robust risk management strategies to mitigate any identified threats effectively.
Mitigating Third-Party Risk through Effective Vendor Management
Effective vendor management can significantly reduce potential vulnerabilities and improve the resilience of a company’s supply chain network against external threats.
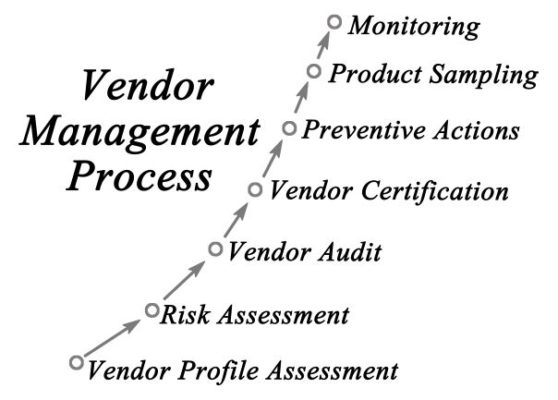
This involves conducting a thorough vendor assessment, identifying any risks associated with the supplier, such as their financial stability, reputation, or compliance with industry standards.
Once vendors have been assessed for risk, companies must negotiate contracts that clearly outline expectations and responsibilities. This includes establishing clear communication channels between both parties and defining specific performance metrics that will be used to measure success.
Additionally, contracts should include provisions that address how disputes will be resolved and what penalties will be imposed if either party fails to meet agreed-upon terms.
Effective vendor management requires ongoing monitoring and evaluation of vendor performance throughout a contract.
Companies can identify potential issues early on by regularly reviewing key performance indicators (KPIs) such as delivery times or quality control measures and take corrective action before they become major problems.
Furthermore, regular communication with vendors can help build stronger relationships between both parties and foster greater collaboration in addressing shared challenges.
Ensuring Compliance with Third-Party Risk Regulations and Standards
Third-party risk is a critical aspect of vendor management that requires constant monitoring and evaluation to ensure that vendors comply with established rules, regulations, and industry standards.
Failure to adhere to these requirements could result in significant financial losses, reputational damage, or legal action against the company.
Risk assessment is an essential component of third-party risk management. It involves identifying potential risks associated with specific vendors and evaluating their likelihood of occurrence and impact on the organization’s operations.
This process helps companies prioritize their vendor management efforts by focusing on high-risk vendors first.
Additionally, understanding the regulatory landscape is crucial for businesses operating in different regions, as each has its unique set of laws governing vendor relationships.
To ensure compliance with third-party risk regulations and standards effectively, companies must establish robust policies and procedures that govern vendor selection, contract negotiation, monitoring, and termination.
These policies should outline how vendors are assessed for risk during procurement and continually monitored throughout their organizational engagement.
Regular audits should also be conducted to evaluate compliance levels accurately.
Ensuring compliance with third-party risk regulations and standards is critical to mitigating potential legal and financial risks associated with noncompliance. Companies must conduct thorough risk assessments while keeping up-to-date with changes in regulatory landscapes to stay ahead of emerging threats posed by external partners/vendors.

Frequently Asked Questions
What are some common examples of third-party risks in different industries?
Vendor selection and due diligence are crucial in mitigating third-party risks across various industries.
In the financial sector, outsourcing services such as IT support or accounting to third-party vendors can lead to potential risks of data breaches or non-compliance with regulatory requirements.
Similarly, healthcare organizations that outsource medical billing and coding services to third-party vendors face the risk of confidential patient information being exposed.
The retail industry also faces third-party risks when outsourcing manufacturing or distribution processes to vendors who may not adhere to ethical labor practices or environmental regulations.
How can organizations effectively assess and monitor third-party risks?
Organizations can use various methods to assess and monitor third-party risks, such as conducting regular audits and assessments of their vendors, suppliers, or partners, reviewing contracts with third parties, and implementing a systematic approach to risk management.
What are the consequences of not properly managing third-party risks?
The consequences of not correctly managing third-party risks can be severe, ranging from significant financial losses to irreparable damage to an organization’s reputation.
Failure to conduct proper due diligence on third-party vendors and suppliers could result in costly legal actions, regulatory fines, and loss of business opportunities.
Moreover, a lack of oversight and control over third-party activities increases the likelihood of data breaches or other security incidents that could lead to the theft or loss of sensitive information.
Such incidents can lead to significant financial impact for an organization and damage its reputation in the eyes of customers, partners, and stakeholders.
What strategies can organizations use to mitigate third-party risks that cannot be eliminated?
Outsourcing challenges and contractual obligations can present significant third-party risks for organizations. While eliminating these risks may not be possible, several strategies can help mitigate them.
One approach is to conduct a thorough risk assessment of potential vendors or partners before entering into any contracts or agreements. This can include reviewing their financial stability, regulatory compliance, and security practices to ensure they align with the organization’s own standards and requirements.
Another strategy is establishing clear expectations and guidelines in contractual agreements, such as outlining specific security measures that must be implemented or requiring regular audits and reporting on compliance.
Additionally, ongoing monitoring and communication with third-party providers can help identify and address any emerging risks or issues before they become major problems for the organization.
How do emerging technologies and trends, such as cloud computing and the gig economy, impact third-party risk management?
Emerging technologies and trends like cloud computing and the freelancer economy have significantly impacted third-party risk management.
With the increasing adoption of cloud services, there are concerns about cloud security risks such as data loss, unauthorized access, and cyber-attacks. Organizations need to ensure that they have robust security measures to mitigate these risks when working with third-party vendors who use cloud technology.
Additionally, the gig economy has created new challenges in managing third-party risks as organizations increasingly rely on freelance workers who may not be subject to the same scrutiny or compliance requirements as traditional employees.
Conclusion
Third-party risk is an essential aspect of business operations that cannot be ignored. It refers to any vulnerability or threat from external entities such as vendors, suppliers, contractors, customers, or partners.
The impact of third-party risk can be detrimental and far-reaching and may manifest as reputational damage, financial loss, legal sanctions, or regulatory non-compliance. Therefore, identifying potential sources of third-party risk remains crucial for organizations seeking to mitigate these risks.
Effective vendor management is one strategy businesses can adopt to manage third-party risks. This involves implementing policies and procedures that govern vendor selection and management throughout the vendor lifecycle.
Additionally, compliance with third-party risk regulations and standards ensure that businesses operate within acceptable thresholds while mitigating potential liabilities.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.

